Vendor Management and Privacy By Design: Part 2
Article Content
In Part 1 of this article, we spoke about a few existing gaps in the way we build contractual relationships. In this part, we are going to talk about the potential impact of ISO Standards, the U.S. cybersecurity order, and how Privacy by Design could be leveraged to create better Vendor relationships.
ISO Standards
Similar to what happens with governance frameworks like COBIT, implementing an ISO standard is often a synonym of trust; it enhances reputation. For this reason, Clients prefer Vendors who are ISO certified or that, at minimum, adhere to a recognized privacy and security framework or standard. Evaluating this point, a Client may determine whether a Vendor is likely to be a good partner and, during the performance of the agreement, how the Vendor is responding to its obligations.
However, as indicated by the Office of the Privacy Commissioner of Canada[^1], implementing the standard and obtaining a certification for a specified period of time doesn’t guarantee that an organization will remain in compliance:
- In the context of this additional knowledge by Equifax Canada, it was therefore not reasonable for it to rely on the ISO 27001 certification as assurance of adequate security by Equifax Inc. Cognizant of such poor practices, Equifax Canada should have taken further measures to assess the security of Canadian personal information held by Equifax Inc. and ensure that any necessary corrective measures were taken in a timely way.
This is a big challenge for Clients relying on these standards to corroborate Vendor’s compliance. It is also where having a closer relationship may allow the Client to gather information from the Vendor to determine if there are issues to be addressed and how to do it in a collaborative manner.
a) ISO 27701
The ISO 27701 standard assumes that the company (Vendor, in this case) abides by ISO 27001, the cybersecurity standard. According to ISO 27701,
§ 5.3.3 Top management shall ensure that the responsibilities and authorities for roles relevant to information security and privacy are assigned and communicated. Top management shall assign the responsibility and authority for: (a) ensuring that the information security and privacy management system conforms to the requirements of this International Standard; and (b) reporting on the performance of the information security and privacy management system to top management.
This requirement and, in general, the contents of the standard, are indicative of a Proactive, not Reactive take on privacy within an organization.
Notwithstanding the foregoing clause, the privacy function is often housed by legal or compliance. As indicated by ISO, top management should be responsible for assigning privacy and security responsibilities; that said, privacy when it pertains to technology Vendors, should be an interdisciplinary effort between several teams depending on the service (design, product, development, security, compliance, legal, and contract functions), each responsible for specific areas, but all required to participate in deciding specific protections and, therefore, contractual language required.
b) ISO 27001
Section A.15 of the Annex to ISO 27001, Supplier Relationships, includes five controls[^2]:
| A.15 Supplier relationships | ||
| A.15.1 Information security in supplier relationships | ||
Objective: To ensure protection of the organization’s assets that is accessible by suppliers. | ||
| A.15.1.1 | Information security policy for supplier relationships | Control |
| A.15.1.2 | Addressing security within supplier agreements | Control |
| A.15.1.3 | Information and communication technology supply chain | Control |
| A.15.2 Supplier service delivery management | ||
Objective: To maintain an agreed level of information security and service delivery in line with supplier agreements. | ||
| A.15.2.1 | Monitoring and review of supplier services | Control |
| A.15.2.2 | Managing changes to supplier services | Control |
After reading these controls, you can see that all of them are addressed through Vendor agreements but, if you consider the invasive nature of controls A.15.2.1 and A.15.2.2, it is reasonable to assume that a pre-condition for a Vendor to willingly agree to such controls is a certain level of trust, which can only be gained through a good relationship that allows a proactive treatment of privacy and security as well as dynamic identification and solution of related issues.
A Step In The Right Direction? Improving The Nation's Cybersecurity
In addressing the issues that have been mentioned in this article but also in Part 1, the government and regulators could be of assistance. As an example, on May 12, 2021, the White House published President Biden’s Executive Order on Improving the Nation’s Cybersecurity. The Order says:
...the trust we place in our digital infrastructure should be proportional to how trustworthy and transparent that infrastructure is, and to the consequences we will incur if that trust is misplaced.
The Order, in section 2, directly indicates that contractual terms or restrictions represent barriers to sharing information that could be used to improve the existing IT ecosystem in order to deter, prevent, and defend from different threats.
While this is applicable to specific Vendors contracting with the U.S. government, the United States is a “trend-setter”, especially for Canada, given the very close trading relationship that binds the two countries. Recognizing that there is a problem with existing contractual clauses (in their case, FAR clauses) could be a huge step towards developing a cooperative model to negotiate and implement privacy and cybersecurity protections.
Thus, we need Vendors to proactively disclose issues in order to address them and mitigate risks (Privacy as the Default Setting & End-to-End Security). For that, we must recognize that our approach to managing Vendor relationships should consider the needs of both parties.
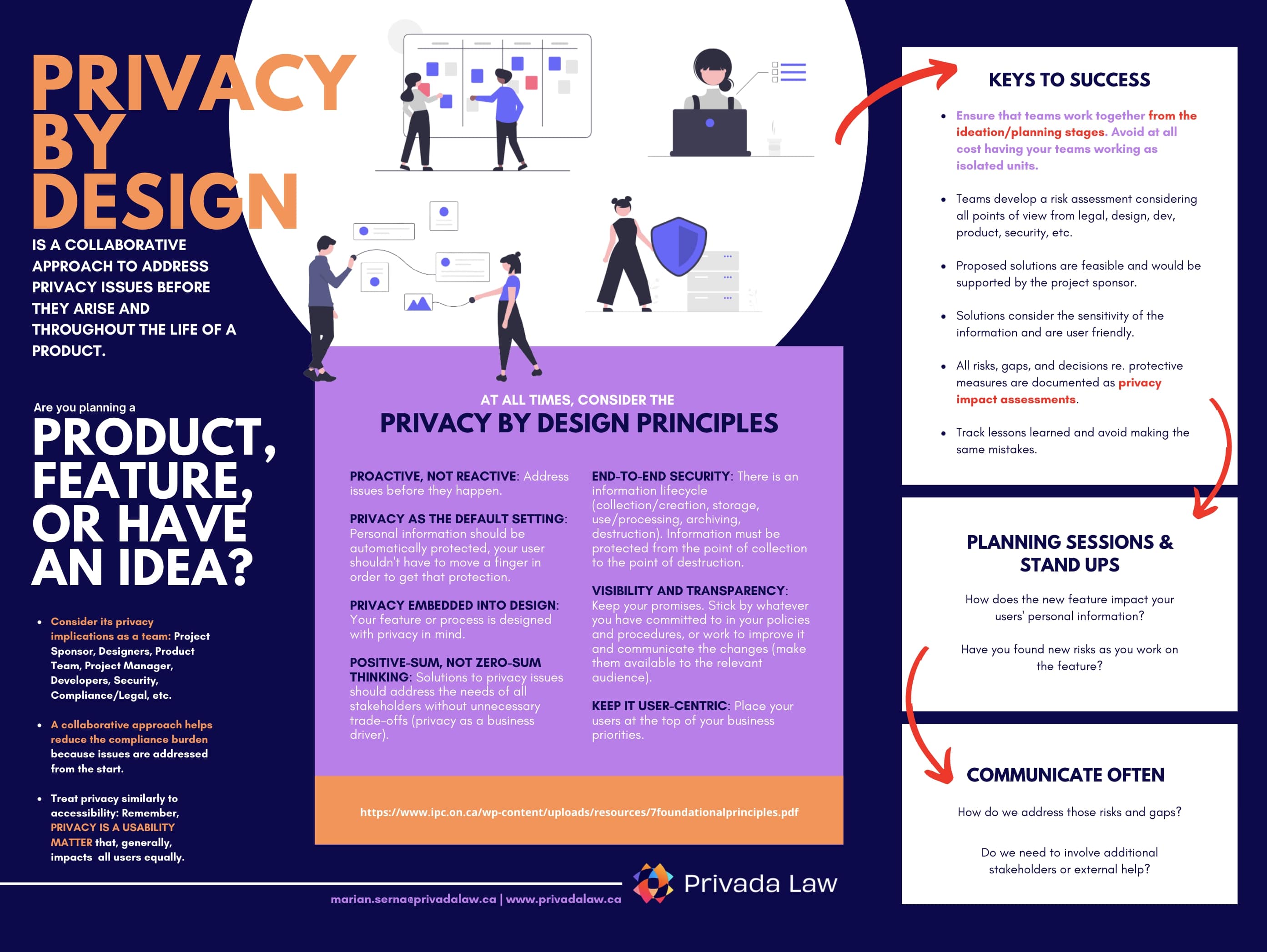
Privacy By Design Findings
All Privacy by Design principles swimmingly translate to Vendor relationship management, a key element to develop and implement a privacy program. However, a company’s culture may stand in the way of collaborative relationships. Clients that look for power-imbalanced relationships in their favour may be hurting themselves: At the time of an incident where the Vendor is involved, it is the Vendor who has the information; therefore, communication with a Vendor that has felt mistreated may not be optimal. Any such issue will interfere with Client’s compliance and will impact its workflows.
-
Proactive, not Reactive
Clients and Vendors should treat each other as allies, setting expectations in order to be able to define each party’s obligations, but also recognizing that both parties will likely need to enhance their privacy protective measures at some point in the relationship and that this will have implications to the party’s bottom line.
-
Privacy as the Default Setting
Trust-based relationships between Client and Vendor go beyond the contract. Having a closer relationship will allow the Client to determine if the Vendor’s service automatically protects user privacy and, at the same time, will permit the Vendor to transparently indicate what improvements, if any, need to be made and how they will be implemented.
-
Privacy Embedded into Design
Relevant stakeholders should understand what business practices can be leveraged to decide what privacy and cybersecurity framework will be applicable and, if needed, design a set of additional privacy protective controls to be implemented having in mind the amount and sensitivity of the personal information to be transferred.
-
Positive Sum, not Zero-Sum
While standardized practices are required to prove that a company’s contract management model is mature, it is worth thinking about what to do if standard practices are becoming a barrier to fluid Vendor relationships that promote collaboration and, as such, standard practices may defeat the ultimate purpose of having a contract which is adequate risk protection. For example, there will be no adequate risk protection if a Vendor feels pressured to lie in the Vendor questionnaire to get the Client.
-
End-to-End Security
As with principle 2, a trust-based relationship will not only facilitate disclosure of potential issues and incidents but it will also put pressure on the Vendor to enhance its security considering the good relationship with the Client and the desire to retain it.
-
Visibility and Transparency
In terms of visibility and transparency, it is necessary for all relevant stakeholders, including legal counsel, to understand the service’s operational impact, as well as the most adequate personal information protective measures based on the way the information is to be treated and the Vendor’s risk profile.
-
Respect for User Privacy
Along traditional ways to determine whether a company respects its users’ privacy, contracts are also a reflection of privacy practices. In order to build a user-centric privacy culture, a company (and especially its lawyers) must understand user needs, engage only Vendors who are committed to protecting the privacy of Client’s users, keep a good relationship with those Vendors, and comprehend the consequences of implementing the Vendor’s system.
[^1]: PIPEDA Findings #2019-001. Retrieved from: https://www.priv.gc.ca/en/opc-actions-and-decisions/investigations/investigations-into-businesses/2019/pipeda-2019-001/ [^2]: ISO/IEC 27001:2013(E), Annex A.
